While sending emails is a straightforward process for individuals, organizations don’t have that luxury. They must put a lot of thought into this process to avoid security threats and ensure all of their emails get to recipients’ inboxes. That’s where email infrastructure comes into play.
Though it operates behind the scenes, it combines all the components that are responsible for sending and delivering emails. Today, we’ll break down what email infrastructure is, how it works, and what can be done to boost its performance.
What is email infrastructure?
Email infrastructure is the set of software and hardware components that are triggered as soon as you write an email and hit the send button. It combines mail servers, agents, and IP addresses – basically everything that you’d need for the successful delivery of email campaigns.
Think of it as a postal system that combines postal offices, staff who sort through mail, in-house or third-party delivery services, and postal carriers who bring mail to your doorstep.
Even though emails are written and sent through the internet, the structure of the infrastructure is rather similar to real-life postal services, a physical location where you can store your servers and IT assets (excluding all servers and authentication protocols, of course). And just as you would implement security measures to protect your postal service office from any incident, you would also need to protect your servers and assets in a sustainable data center to ensure their uptime.
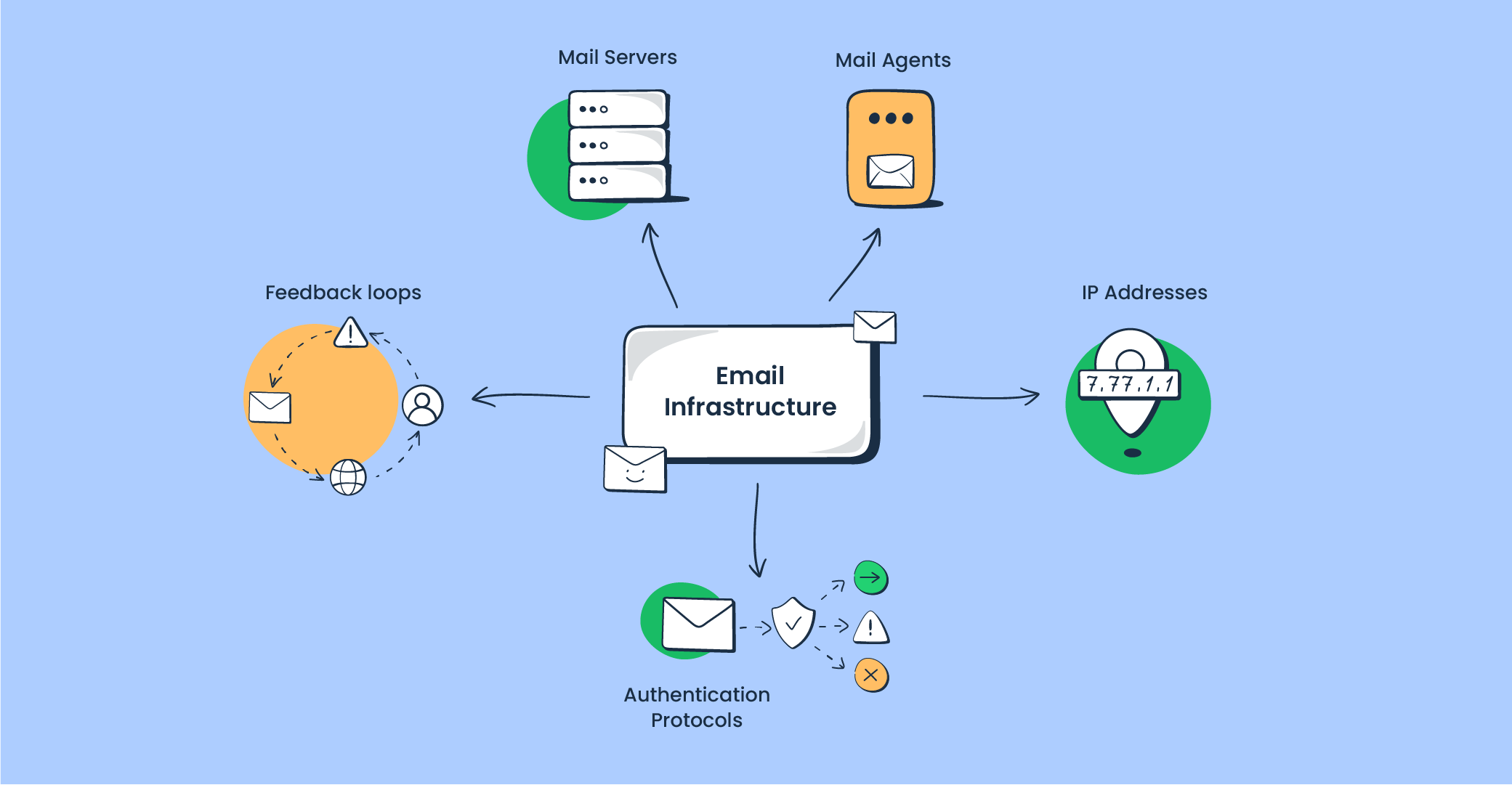
Why would you care about email infrastructure?
Let’s say you have a paper invitation to deliver to your colleague. You drop the letter in the mailbox, but it doesn’t get picked up on time. While you’re waiting for the mail carrier, someone breaks into the mailbox, changes the letter’s content, and disappears.
The letter gets delivered to the recipient eventually, but instead of containing an invitation to the New Year’s Party, it asks your colleague to donate money to the swindler’s bank account.
That’s exactly how phishing attacks are executed in the world of electronic mail. Weak email infrastructure becomes an easy target, allowing attackers to hijack reputable email addresses, forge the content of emails, and deceive recipients. Such attacks are not only harmful for the recipient, but they also have dire consequences in terms of data privacy and protection.
Another point to remember here is that poorly-executed email infrastructure can have a direct impact on sender reputation, causing the recipient’s email client to think that your domain isn’t secure and mark it as spam, reducing the deliverability rate of your transactional emails.
Email infrastructure architecture
Email infrastructure consists of the following elements: mail agents, mail servers, authentication protocols, IP addresses, sending domains, and feedback loops.
Mail agents
Mail agents are vital components of email infrastructure as they take care of the whole process from sending to transferring to delivering the emails and showing them to the recipient. Typically, four types of mail agents are used to send emails: MUA, MSA, MTA, and MDA.
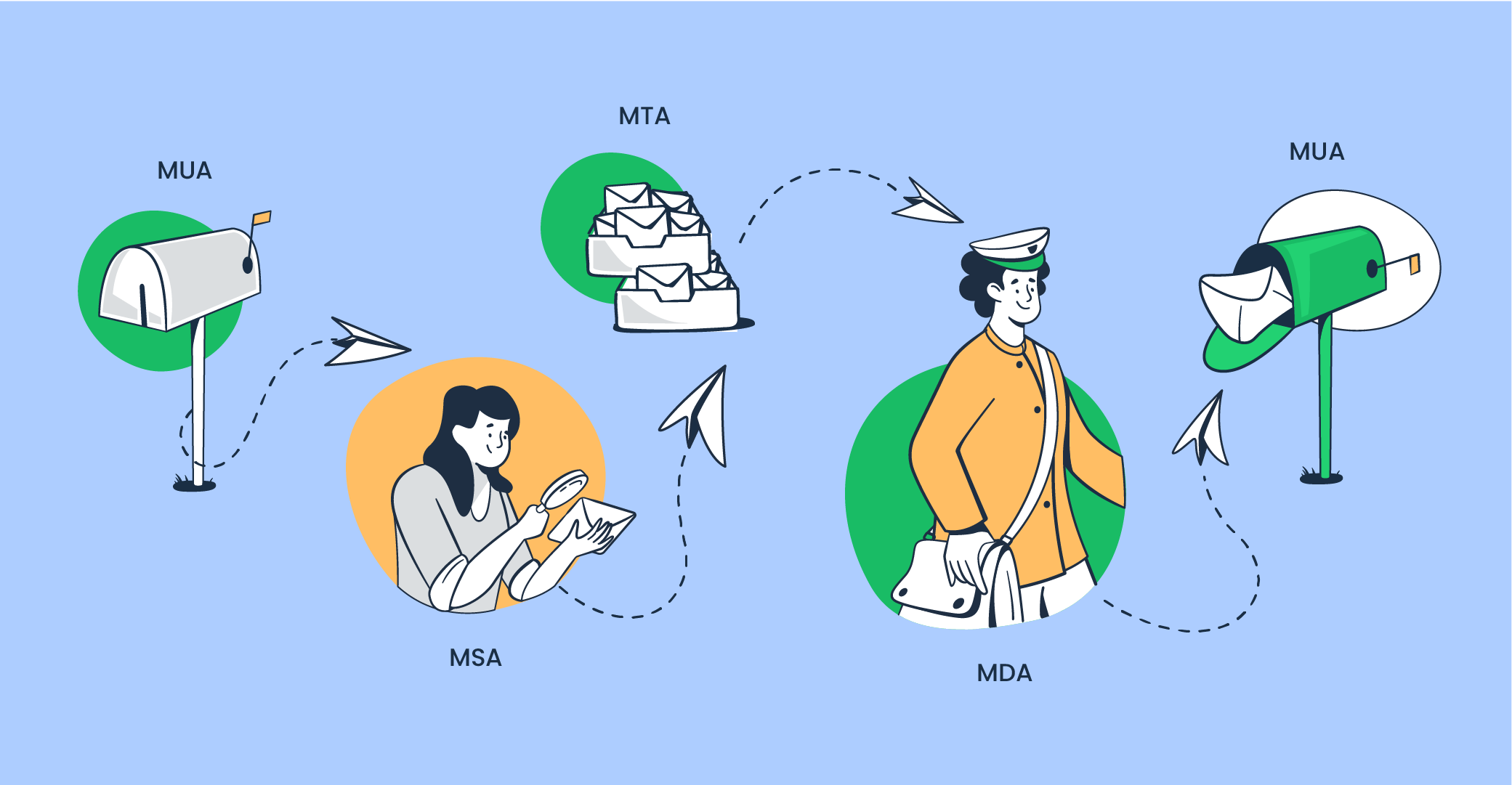
Mail User Agent (MUA)
Mail user agent, otherwise known as email client, is a web-based or desktop application that users use to retrieve, read, send, or receive emails. They also make it possible to delete unwanted messages or flag them as spam. The most common MUAs include Google Gmail, Microsoft Outlook, and Mozilla Thunderbird, among others.
In real life, an MUA would be a local post office or mailbox to which you submit the mail you’re willing to send.
Mail Submission Agent (MSA)
Mail submission agent acts as an intermediary between the mail user agent (MUA) and the mail transfer agent (MTA). It receives the message from the email client, checks it for errors, and, if everything’s okay, transmits it to MTA.
Think of MSA as a post office counter clerk who checks whether your and your recipient’s addresses are indicated correctly on the envelope.
Mail Transfer Agent (MTA)
After receiving the message from MSA, mail transfer agent or email relay transmits messages to another computer. If the recipient’s email address is on the same server, the email will proceed to the next step in the delivery process.
However, most of the addresses aren’t. In that case, email relay or SMTP relay comes into play: MTA looks up the recipient’s domain and, if there’s a match, transfers the message to another MTA.
If we circle back to the paper mail, MTA would be the mail processing plant where the letters are sorted depending on which neighborhood they are addressed to. If the recipient’s address is in the same city, the letter will be delivered right away. If not, it might be sent to another mail processing plant or MTA closer to the recipient’s address.
MTA is also a crucial component in email queuing while sending emails in bulk. Email queuing is the process of holding off emails on the SMTP server and putting them in a sort of buffer until the recipient is ready to receive them. Email queuing is a natural process that makes it possible to prioritize certain emails (e.g., password change confirmation) over others (e.g., weekly newsletter).
For more information on MTAs, check out our dedicated tutorial:
Message Delivery Agent (MDA)
Once the message goes through all the MTAs, it is passed to the message delivery agent, which converts received messages into the appropriate format and transfers them to the recipient’s MUA. In the best-case scenario, messages will end up in the recipient’s inbox. However, if the sender’s domain reputation is low or the authentication fails, messages will go to the spam folder or get discarded.
MDA would be the mail carrier who picks up mail from the recipient’s post office and delivers it to their mailbox (MUA).
Mail servers
It’s virtually impossible to send an email without email servers. There’s only one outgoing server called SMTP server, and two inbound servers: IMAP and POP3.
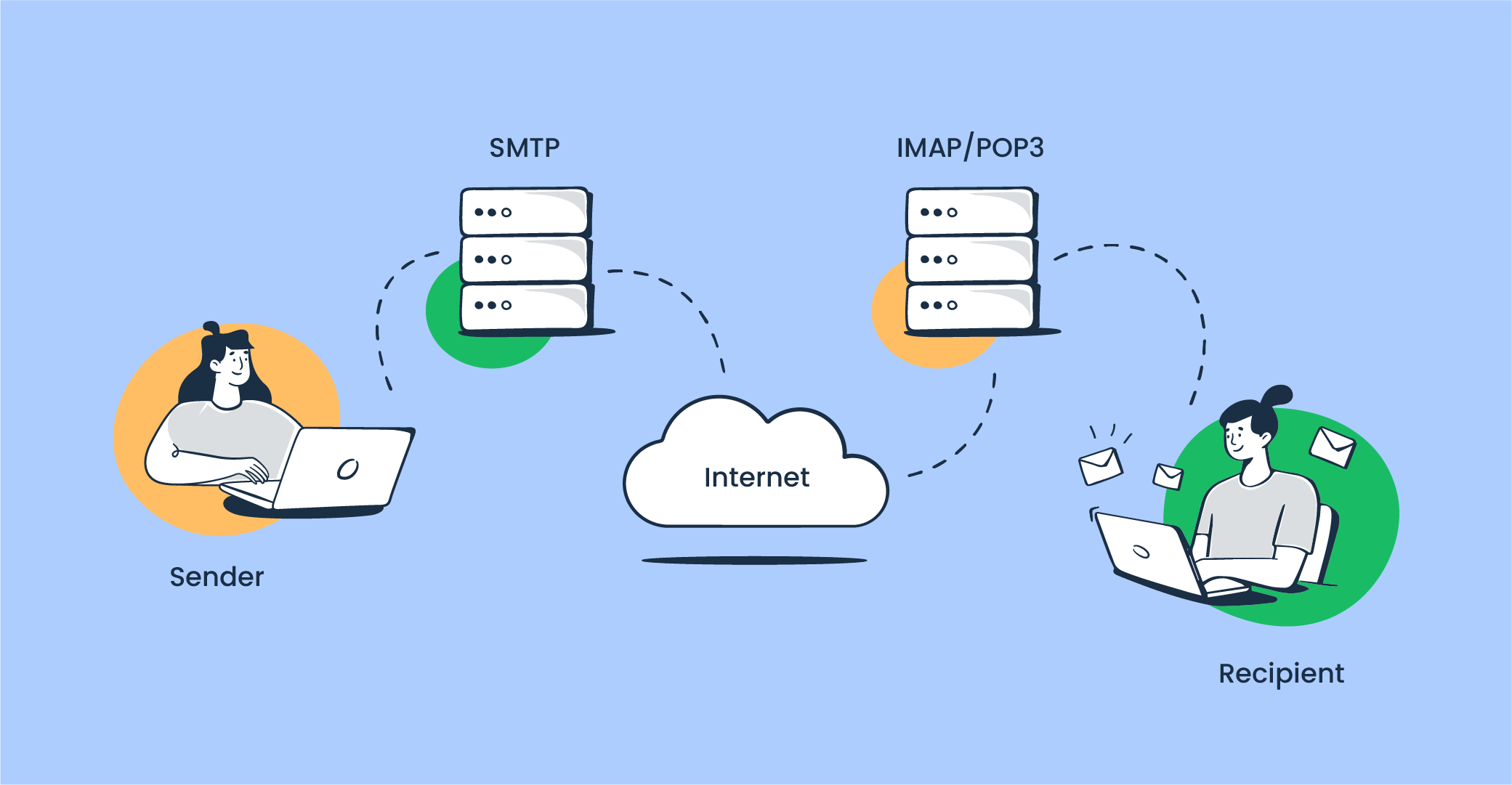
SMTP server receives the messages from MUA and conducts authentication checks through DNS records to verify the recipient’s email address. If any of the checks fail, the email will bounce back or end up on the email blacklist (if the email reputation is low).
If the authentication is successful, emails are delivered through mail agents to the recipient’s inbound mail server, either IMAP or POP3, depending on which one is set up.
IMAP stores received messages on the server and downloads them once the recipient retrieves them from the inbox, saving the copy within the server. This is the option most email clients incorporate into their email infrastructure.
POP3 also stores messages on its servers, but it deletes them as soon as the recipient retrieves their emails. It’s less dependent on an internet connection since the messages are downloaded at once and can be accessed even offline.
IP address
An IP address, otherwise known as an Internet Protocol address, is a combination of numbers (or numbers and symbols in the case of new addresses) that locates and identifies nodes within the computer. It’s a numerical address of the domain, determined by Domain Name System (DNS). IP addresses are generally vulnerable to cyberattacks, if exposed. That’s why businesses use VPN, in addition to other authentication protocols to secure their network.
Thanks to DNS, alphabetical names of domains (mailtrap.io, google.com, etc.) can be translated into numerical IP addresses (192.158.1.38.) in seconds. IPs are essential for communication and data sharing between networks and computers i.e. they are vital to internet operation.
There are two main types of IPs: shared and dedicated.
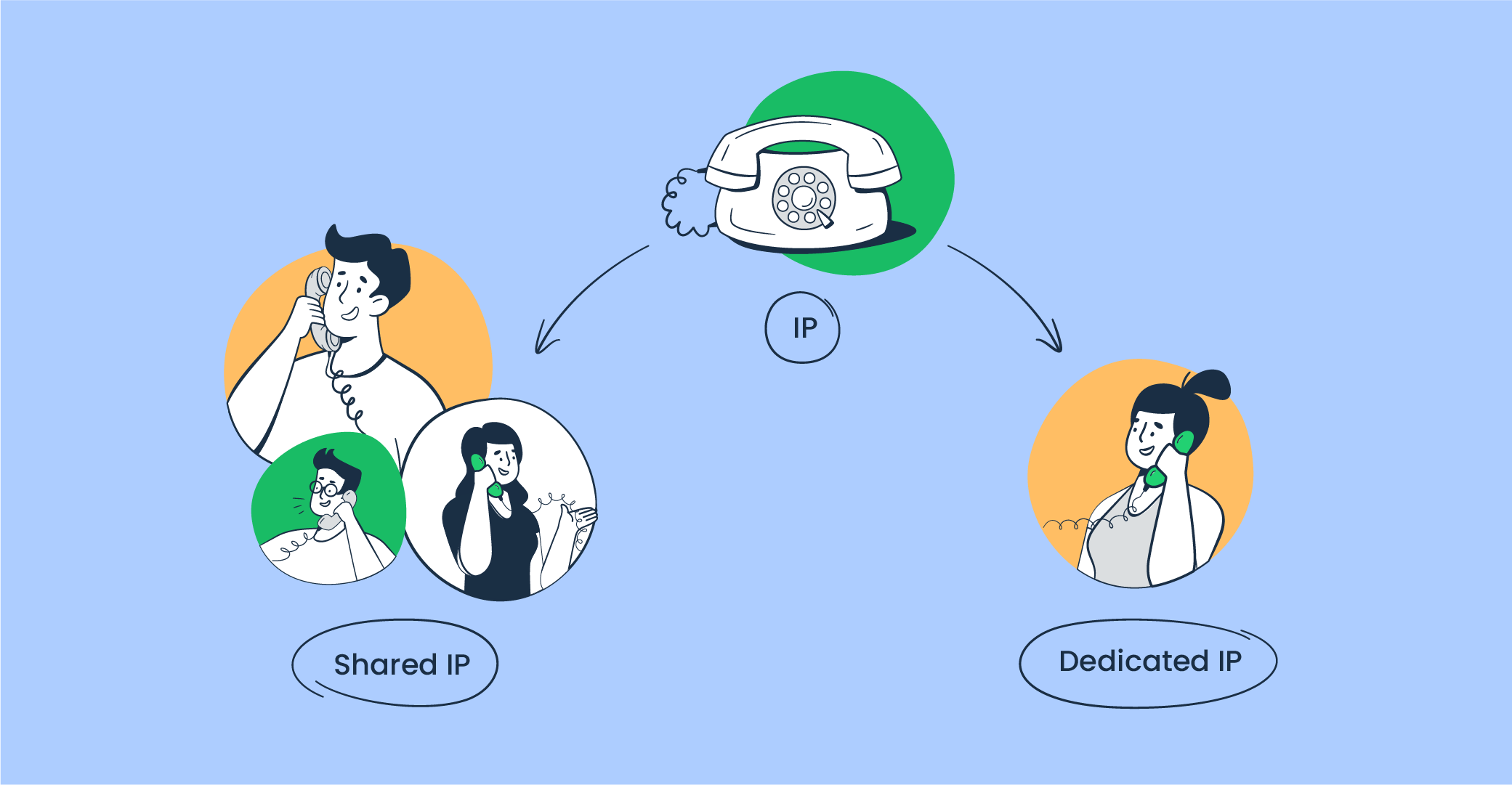
Shared IP is an IP address that is used by multiple domains at once. It’s usually provided by the Internet Service Provider (ISP). It is mostly suitable for individual users or small businesses that send small amounts of emails. Those who use shared IPs are more vulnerable to the other users’ actions as those could be spammers who don’t follow email sending protocols, affecting email sender reputation negatively.
A dedicated IP is an IP address that is allocated to a particular website domain. It’s a more secure option and is widely used by larger organizations that send thousands of emails daily.
Dedicated IPs are more likely to pass spam filters, maintaining a good sender reputation and improving email deliverability, particularly in corporate email infrastructure.
However, to achieve all those results, it’s necessary to use IP warming. IP warming is the process of building trust among email service providers. Once the dedicated IP is created, the user should start sending small batches of emails in a specific schedule, increasing the amount slowly. That way, the IP will gradually warm up, and the domain reputation won’t be compromised.
If you’re interested in more details, check out our blog post about dedicated and shared IPs as well as our Mailtrap YouTube tutorial.
Sending domains
A sending domain is the domain that tells the servers who is sending the emails. It’s the part of the email address that comes after the ‘@’ symbol.
Similar to IP addresses, sending domains can also be shared and dedicated.
Shared domains are usually associated with free email accounts, such as @gmail.com or @yahoo.com, for example.
Dedicated sending domains are unique and represent brands or companies, for example, @mailtrap.io. The biggest advantage of such sending domains is that domain owners have full control over DNS records. This means they can add authentication protocols and show email servers that they are legitimate senders.
Moreover, dedicated sending domains allow businesses to build their reputation from scratch and maintain it, without getting affected by other senders’ behaviors.
Just like IPs, you should warm up sending domains. Sending domain warmup will usually be way quicker than IP warmup.
Authentication protocols
Email authentication protocols are ‘defense mechanisms’ used by the recipients’ servers. They ensure that the message wasn’t hijacked, altered, or forged before getting delivered. To validate the accuracy and authenticity, most modern servers use the following protocols:
- SPF: a basic protocol that is used to check if the sender’s IP is authorized. SPF has a TXT format and is stored in DNS records. The recipient’s server will scan DNS to check if the IP belongs to the list of authorized IPs. If so, the email will be delivered. If the authentication fails, the message will be either flagged or rejected.
- DKIM: a type of digital signature that is included in the email’s source code to check if the sender’s domain is authorized and verify that the contents of the email weren’t altered. DKIM utilizes a set of tags and characters to create a hashed private key. Once the email gets to the receiving server, it searches for the corresponding public key. If there’s a match between public and private keys, the authentication will be successful.
- DMARC: a more advanced authentication method that utilizes either or both SPF and DKIM. While setting up DMARC, the domain owner can choose which of these protocols will be used for authentication and how ‘strict’ the validation process will be (whether the domains should be the exact match or subdomains are also allowed). DMARC protocol enables domain owners to improve their sender reputation gradually by instructing the receiving server on what to do if authentication fails (quarantine, reject, or nothing). It sends reports of each failed authentication and allows for a quick response in case the sender domain gets spoofed.
- BIMI: the newest of the authentication protocols that uses DMARC but adds another layer of security by validating brands’ logos. If BIMI is set up, DNS will include the TXT record with information about the brand’s logo. The recipient will see that logo when they receive the email from that brand. BIMI isn’t widely adopted yet as it’s still being tested by email providers.
While setting up your email infrastructure, it’s necessary to decide which authentication protocols will be used for domain verification. Remember that only one protocol might not be enough – it’s better to implement the combination of all of them to protect your domain and IP reputation. We’ve developed free tools to help you keep an eye on your own email infrastructure. Try them out:
- SPF Record Checker
- DKIM Record Checker
- DMARC Record Checker
- IP Blocklist Checker
- Domain Blocklist Checker
Feedback loop
Email feedback loop (FBL) is another important component of email infrastructure. It enables organizations to receive data about users’ spam complaints from email service providers (ESPs).
By doing so, senders get the chance to remove clients who are no longer interested in their content from their email list. Spam complaints are a nightmare for any email marketing campaign as they affect sender reputation and cause deliverability issues.
However, not every user is eligible for FBL registration. It’s not provided by every Internet Service Provider (ISP) either. To qualify for FBL, business owners should satisfy the following criteria:
- Be the owner of the IP or domain or have admin rights;
- The Reverse DNS of the IP should be the same as the one you’re using;
- Have a functional postmaster@ or abuse@ email address for the domain for reporting spam or errors;
- Have a good reputation (can be observed and maintained with the help of reputation management tools).
What are the types of email infrastructure?
The most common types of email infrastructure are managed and self-managed:
- Managed email infrastructure is managed by third-party providers. They handle analytics, scaling, and the stability of email infrastructure for you. Most third-party email providers, such as Mailtrap, Mailgun, SendGrid, Postmark, and others, provide managed email infrastructure. This option is suitable for most businesses using emails as the communication channel.
- Self-managed email infrastructure is managed by the specific organizations themselves. All the hardware and software components are handled in-house, including analytics, scaling, and maintenance. This is quite challenging and requires a lot of resources, especially if sending volumes are high. Self-managed email infrastructure is usually reserved only for organizations that deal with confidential data (such as military, government, or healthcare organizations). In such cases, healthcare app development services can play a key role by integrating secure communication channels within the email infrastructure and maintaining compliance with healthcare regulations.
How to improve performance and scalability of email infrastructure?
The easiest way to improve the scalability of your infrastructure is to use cloud-based services and scale them horizontally. Horizontal scaling means adding new MTAs in the infrastructure to decouple operations and send high volumes of emails. It’s also a good idea to leverage out-of-the-box service scalability offered by most cloud providers. To boost performance, optimization of the testing workflow is the industry best practice and the most viable solution.
You can read more about service scalability in our upcoming blog post.
What is email infrastructure as a service, and should you use it?
Email infrastructure as a service is a third-party solution that provides secure and scalable servers for sending email communication. The most popular options include:
If you like to find out more about the email deliverability rates of each provider, check out our email deliverability comparison test.
While most of these SaaS solutions have similar features, Mailtrap Email Delivery Platform offers additional benefits. It’s an end-to-end sending solution that allows developers to test, send, and control emails within a single platform.
Mailtrap Email API/SMTP is widely used to send bulk emails to the recipients’ inboxes. It enables users to store logs for 60 days and set up email categories (welcome emails, confirmation instructions, and so on) to analyze their performance in depth. Categories can be filtered depending on mailbox providers and sending domains, with color-coded charts showing the performance of each.
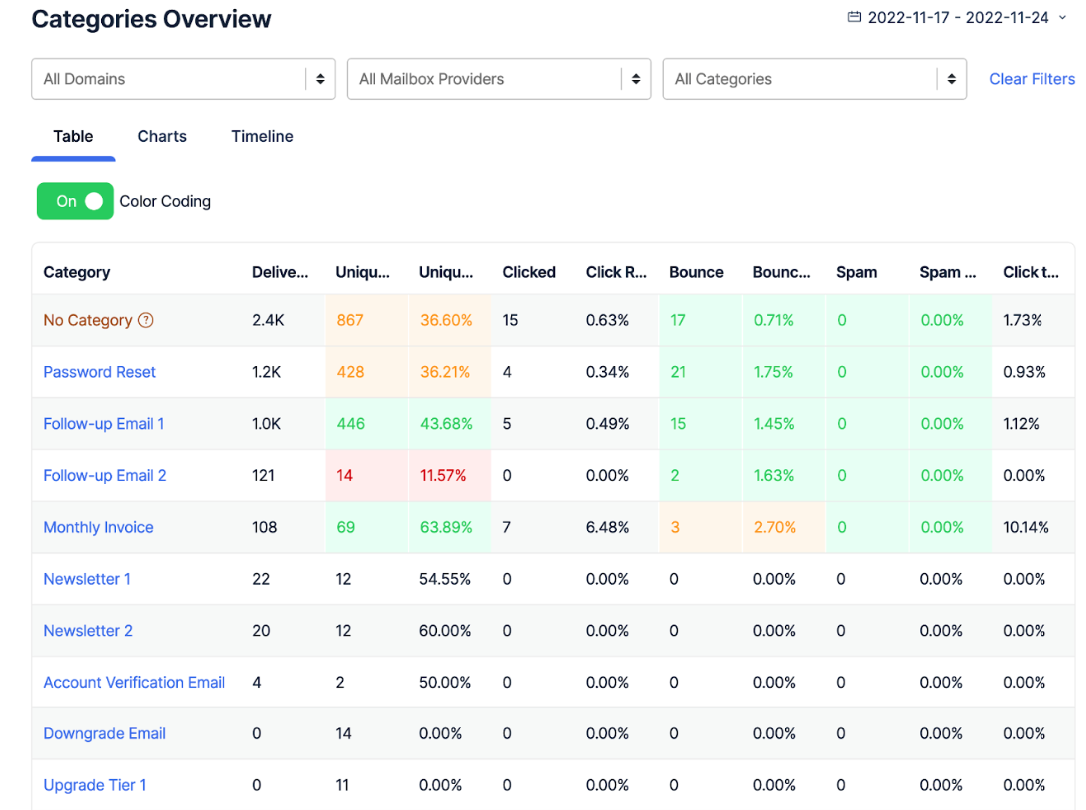
Email API is an effortless email infrastructure solution as it takes a lean approach to onboarding. You can verify your domain and start sending emails without building sender identity and answering lengthy questions. Once the domain is verified, you can set Mailtrap as an SMTP or use its API with ready-made code snippets in different programming languages.
You can learn how to migrate your infrastructure from one provider to another by watching our dedicated video: